Public client support with PKCE added to the OpenID Connect client for developers
The OpenID Connect client for test driving IdP servers, including ours, received a bunch of improvements and can now pose as an unauthenticated (public) client, with optional PKCE security.
With that you can now choose between the following client authentication methods:
- client_secret_basic -- The default HTTP basic authentication
- client_secret_post -- Like basic, but using HTTP post instead of the Authorization header to submit the client credentials
- client_secret_jwt -- Client authentication by means of a HMAC JWT assertion.
- none -- For public clients.
Client authentication in OpenID Connect is defined in section 9 of the OpenID Connect Core 1.0 spec.
If you're not familiar with the dev client, you can try it out on our demo server. The UI is simple and intuitive. There are just three panes:
1. Set the OpenID provider endpoints
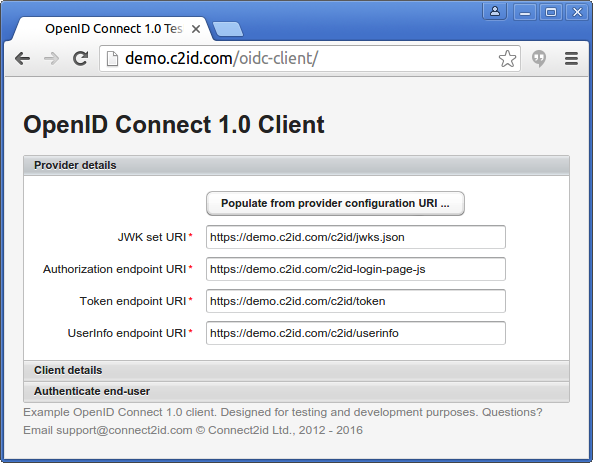
Simple form to enter the OpenID Provider (OP) endpoints. If the OP supports discovery, you can just enter the OP's URL and the client will automatically fetch the discovery JSON and populate the required parameters.
2. Set the client credentials and callback
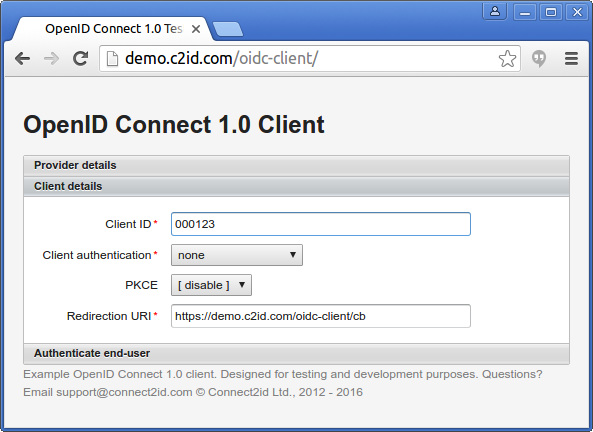
Enter the client or Relying Party (RP) credentials and callback URI. For a public client select none in the client authentication dropdown list. Then you have the option to enable PKCE as well.
3. Make the actual request
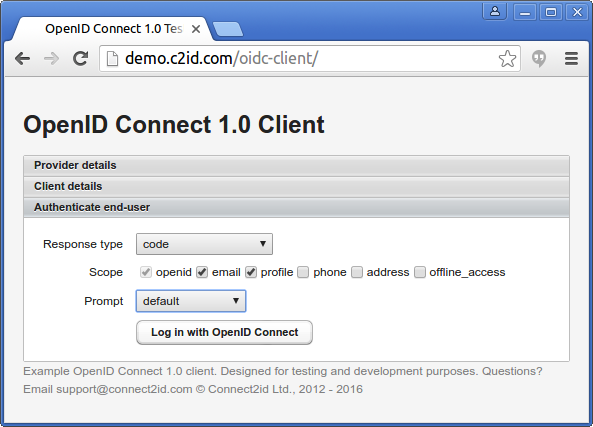
With all required provider and client details in place, you can now make the actual OpenID authentication request by triggering a redirect to the IdP via a browser popup window. You have all key request parameters to play with - the requested scope, the response type (for code, implicit or hybrid flow) and prompt.
4. Receive and process the token(s)
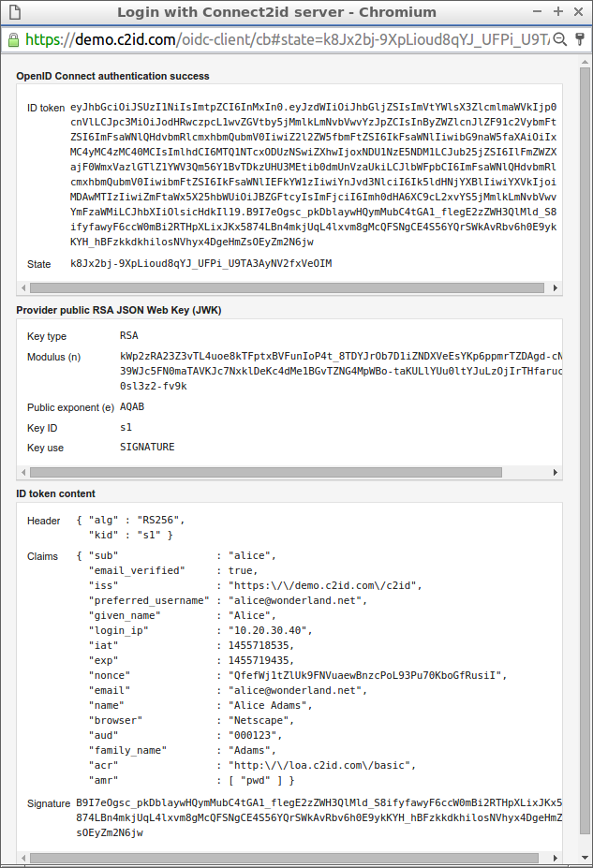
The OpenID server will respond by invoking the registered callback for the client. You can see a breakdown of the code-for-token exchange (in case you requested a code flow), and retrieving the requested claims from the UserInfo endpoint.
The ID token will also be verified and its content displayed.
Download
If you want to install the dev OpenID Connect client on your own computer or server download a ready WAR package for the latest 1.4 version:
https://bitbucket.org/connect2id/openid-connect-dev-client/downloads
From the Git repo you can also obtain the source code. If you wish to contribute, just drop us an email (to Connect2id support), or submit a pull request.
This is our wishlish:
Support for private_key_jwt client authentication.
Support for the claims, id_token_hint and other optional OpenID parameters.
Form for dynamic client registration.
