Updated RP-initiated logout in Connect2id server 12.15
The Connect2id server logout endpoint, used to implement single logout across participating applications, received an update to make it compliant with the latest 02 revision of the OpenID Connect RP-Initiated Logout 1.0 spec.
The logout endpoint can now support ID
token hints (id_token_hint) encrypted for confidentiality. There is also
support for a logout_hint parameter, similar to the login_hint in OpenID
authentication requests, and a ui_locales to personalise the logout UI.
Relying parties that for some reason cannot save the user’s ID token in order
to pass it later in the id_token_hint logout parameter, can use a client_id
to at least hint the application’s identity. The logout session
API, which lets Connect2id
server deployments implement a logout UI, journeys and policies around logout,
was updated to reflect the changes.
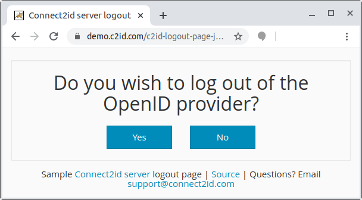
The mini guide for developing a logout UI and the sample project were also revised.
Other changes
The plugin SPI for verifying qualified certificates in a
private_key_jwt
client authentication was also updated to allow for custom error_description
and error_uri fields when an invalid_client error is returned.
Connect2id server deployments that use DynamoDB receive a new optional dynamodb.enableContBackups configuration property, to enable point-in-time recovery (PITR) for all tables where crucial or long-lived server data is persisted. Note that when continuous backups are enabled they will not apply to sessions, codes, caches and other transient data, as there is no practical utility in recovering such data. If you want to have PITR for that data, it must be enabled directly via the AWS APIs for those DynamoDB tables.
You can find detailed information about the changes in Connect2id server 12.15 in the notes below.
Download 12.15
For the signature validation: Public GPG key
Standard Connect2id server edition
Apache Tomcat package with Connect2id server 12.15: Connect2id-server.zip
GPG signature: Connect2id-server.zip.asc
SHA-256: 16af5e3afa5e4810f7df7a204c1206ed9d6eafe66ac2bf5ecd6935e556d129f0
Connect2id server 12.15 WAR package: c2id.war
GPG signature: c2id.war.asc
SHA-256: 8d3feaa7da130f19866ff9fe498a9cbcf440f243d1a23d06eaec733d815a79f9
Multi-tenant edition
Apache Tomcat package with Connect2id server 12.15: Connect2id-server-mt.zip
GPG signature: Connect2id-server-mt.zip.asc
SHA-256: 79c3b72dd0601ef4e583a7174ae27e4c48e2f5d6e490f9dba14e0a99d48b51f3
Connect2id server 12.15 WAR package: c2id-multi-tenant.war
GPG signature: c2id-multi-tenant.war.asc
SHA-256: 2bee27a9d1a131c11c86fe433e768877ac7d35f43f846fbd3c722b85c0be3956
Questions?
If you have technical questions about this new release contact Connect2id support. To purchase a production license for the Connect2id server, renew or upgrade your support and updates subscription, email our sales.
Release notes
12.15 (2022-07-17)
Summary
-
Updates OpenID Connect RP-Initiated Logout 1.0 support to draft 02. Introduces new
logout_hint,client_idandui_localesrequest parameters. See https://openid.net/specs/openid-connect-rpinitiated-1_0.html -
PrivateKeyJWTCertificateVerifier SPI plugins can override the default
error_descriptionanderror_uriininvalid_clienterrors returned to the authenticating OAuth 2.0 client. -
New
dynamodb.enableContBackupsconfiguration property to enable DynamoDB continuous backups / point-in-time recovery for tables holding crucial or long-lived Connect2id server data. Previously continuous backups could be enabled only via the AWS CLI, SDK, API or web console.
Configuration
-
/WEB-INF/infinispan-*-dynamodb.xml
- New
dynamodb.enableContBackupsconfiguration property of type boolean (true|false) to enable continuous backups / point-in-time recovery for all DynamoDB tables where crucial or long-lived Connect2id server data is persisted:id_access_tokens,long_lived_authorizations,revocation_journal,clients,federation_clientsandtenants(in the multi-tenant Connect2id server edition). Applied at Connect2id server startup on new table creation as well as for existing tables. The default value isfalse(no continuous backups).
- New
Web API
-
Logout (end-session) endpoint
-
id_token_hint – Relying parties can submit ID token hints encrypted with JSON Web Encryption (JWE) for confidentiality. The ID token can be encrypted with a public encryption RSA or EC JWK published at the Connect2id server’s
jwks.jsonendpoint. A relying party that is provisioned with aclient_secretcan alternatively encrypt the ID token with a symmetric AES key using the JWEdiralgorithm and a JWE method listed in theid_token_encryption_enc_values_supportedOpenID provider metadata field, as specified in OpenID Connect Core 1.0 incorporating errata set 1, section 10.2. -
client_id – New optional RP-initiated logout request parameter, of type string, representing the client ID of the relying party. A relying party should use it to identify itself in a request when the recommended
id_token_hintparameter isn’t included or when theid_token_hintrepresents a symmetrically encrypted (JWE) ID token so the OpenID provider can resolve the relying party’s registeredclient_secretnecessary for the ID token decryption. If bothid_token_hintandclient_idare included in a logout request the client ID must be found in the ID token audience.Note, a valid
id_token_hintremains required for RP-initiated logout requests that include apost_logout_redirect_uriparameter. -
logout_hint – New optional RP-initiated logout request parameter, of type string, representing a hint about the end-user that is logging out, such as the user’s email address, telephone number or username. Analogous to the
login_hintOpenID authentication request parameter. -
ui_locales – New optional parameter, of type string and consisting of one or more space delimited BCP47 (RFC 7231) language tags, representing the end-user’s preferred languages and scripts for the logout UI.
-
-
/logout-sessions/rest/v1/
-
Adds support for the optional
client_idRP-initiated logout request parameter. The Connect2id server will use it to identify the calling relying party when the recommendedid_token_hintlogout request parameter isn’t included or represents an ID token that is symmetrically encrypted with aclient_secret. If bothid_token_hintandclient_idare present in a logout request the Connect2id will check the ID token was issued to theclient_id; if not aninvalid_id_token_hinterror will be returned. -
New
id_token_hint_presentparameter in the logout prompt message, of type boolean (true|false), to show if the relying party included anid_token_hintin the logout request.Note, if the
id_token_hintlogout request parameter failed the Connect2id server verification (covers all standard ID token checks, save for itsexpclaim), the logout session API will return aninvalid_id_token_hinterror. Hence, theid_token_hint_presentwhen true will always indicate a valid ID token. -
New optional
op_logoutparameter in the logout confirmation message, of type boolean (true|false) and a default valuefalse, to indicate an end-user request for IdP-wide logout in addition to confirming the RP logout. This new parameter deprecates the existingconfirm_logoutparameter. -
New optional
logout_hintparameter in the logout prompt message, of type string, representing thelogout_hintRP-initiated logout request parameter. -
New optional
ui_localesparameter in the logout prompt, logout end and logout error messages, of type string array, representing theui_localesRP-initiated logout request parameter. -
New
invalid_requesterror code to indicate an invalid RP-initiated logout request.
-
SPI
-
Upgrades the Connect2id server SDK to com.nimbusds:c2id-server-sdk:4.49
-
New ExposedInvalidClientException class that extends the common InvalidClientException for representing OAuth 2.0 invalid_client errors, to indicate that the default Connect2id server error_description and error_uri must be overridden with specific values.
The Connect2id has a security policy to log the message of InvalidClientException instances and return a general error_description in the HTTP 401 Unauthorized response that doesn’t reveal the exact cause why client authentication failed. The new ExposedInvalidClientException lets client authentication related plugins override this policy and set the error_description and error_uri in the HTTP 401 Unauthorized response. This facility must be used judiciously.
-
Connect2id server plugins implementing the PrivateKeyJWTCertificateVerifier SPI can throw the new ExposedInvalidClientException instead of the common InvalidClientException to override the default Connect2id server error_description and error_uri in the resulting HTTP 401 Unauthorized response.
When using the ExposedInvalidClientException to set a custom invalid client error_description care must be taken not to divulge sensitive or more information than necessary.
-
Resolved issues
-
Updates the access token (as subject_token) introspection in token exchange grant handling (RFC 8693) to mark tokens which client_id doesn’t match the client_id of the requesting OAuth 2.0 client as invalid. In addition, an OP6216 warning will be logged when this condition is encountered (issue server/768).
-
The logout session web API must not log request query strings at INFO level (issue server/770).
Dependency changes
-
Upgrades to com.nimbusds:c2id-server-sdk:4.49
-
Upgrades to com.nimbusds:oauth2-oidc-sdk:9.38
-
Upgrades to com.nimbusds:lang-tag:1.7