Graphite metrics reporting in Connect2id server 3.8
Graphite metrics reporting
The Connect2id server collects over 100 metrics on the usage of OpenID Connect single sign-on and the various OAuth grants. Admins are also provided with metrics to monitor the live performance of the server. Until now to get at that data you could either query the monitoring endpoint, or fetch it via a JMX dashboard.
The latest edition of the Connect2id server adds a third convenient option - streaming the metrics at an interval of your choice to a remote Graphite system. Graphite has become quite popular with admins and devops as of late, not least thanks to the powerful vis tool called Graphana.
To enable Graphite reporting edit the WEB-INF/monitor.properties file. In
addition to the server host / port where the metrics are to be streamed, you
can also set a polling interval and multiple filters (with wild cards) to
send only those metrics that are actually needed.
Check out its config manual for a detailed explanation of the parameters.
Example Graphite configuration:
monitor.graphite.enable = true
monitor.graphite.host = carbon.example.com
monitor.graphite.port = 2003
monitor.graphite.reportInterval = 60
monitor.graphite.batchSize = 0
monitor.graphite.prefix = 31367e19-7a91-4bca-b457-9daca1f8ae3c.node1
monitor.graphite.ratesTimeUnit = SECONDS
monitor.graphite.durationsTimeUnit = MILLISECONDS
monitor.graphite.filter = *
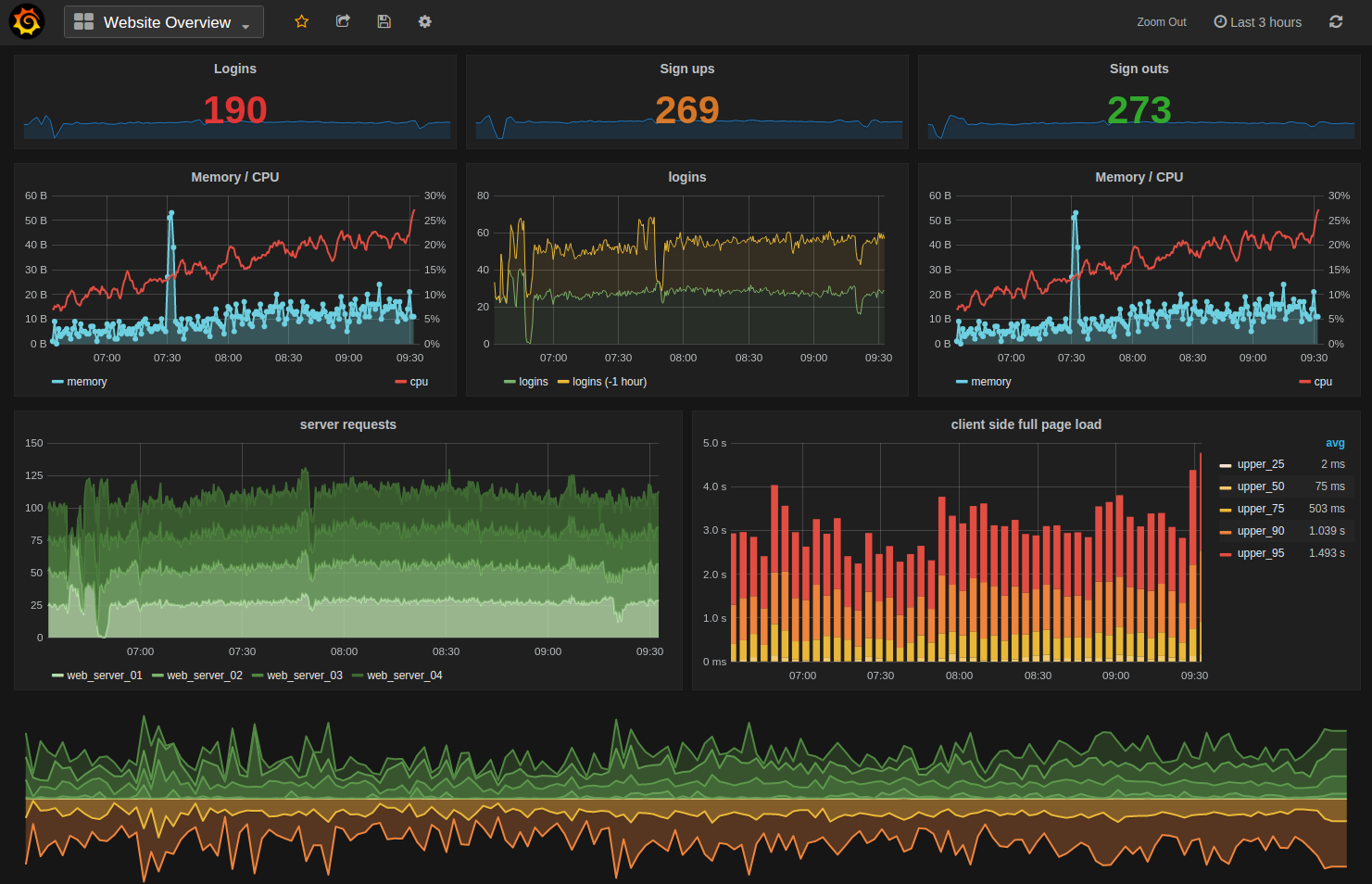
Here is an example screenshot to show you what Graphite / Graphana are capable of. It does take some time to set them up, so you want to get started quickly take a look at Hosted Graphite, which is subscription based.
Client registration management
The Connect2id server provides a standard endpoint where OAuth clients are registered before they can request ID or access tokens from it.
You have various ways to manage client registrations:
-
The manual way. Install a developer portal and manage registrations via it. The dev portal submits the approved client details to the registration endpoint, which is otherwise inaccessible to the outside world. This is the traditional approach for web apps, or apps that are confined within an enterprise.
-
For mobile apps distributed via store. This method allows a mobile app client distributed via a store or similar channel to register itself dynamically with the Connect2id server. To manage this process the mobile apps can be provisioned with a software statement, a registration pass (a signed JWT) that also locks down specific registration parameters, such as the grant types and scope values that the client may register itself for.
-
Pre-approved dynamic registration. The Connect2id server can also issue one-time tokens to register a client, which scope can be tailored to lock down registration to some permitted OAuth grants and other parameters.
-
Some combination of 1, 2 and 3. Note that 2 and 3 overlap in many ways. They can also be automated services.
The latest release of the Connect2id server extends the special scopes for the initial registration tokens to allow scope values to be locked down.
This is best illustrated with an example:
Let’s say you want to issue an initial reg token to permit an OAuth client to make password grant requests for tokens with read and write scopes. In that case give the initial reg token the following scope values:
client-reg:grant:password
client-reg:scope:read
client-reg:scope:write
Don’t hesitate to contact Connect2id support if you think you need help with setting up an optimal and secure client registration for your system.
LDAP server response timeouts
Finally, two new configuration parameters were added to set an explicit timeout for LDAP responses from the directory backend:
-
For the client store: op.reg.ldapServer.responseTimeout
-
For the authorisation store: authzStore.ldapServer.responseTimeout
Download
To download a ZIP package of Connect2id server 3.8:
https://c2id-downloads.s3.eu-central-1.amazonaws.com/server/3.8/Connect2id-server.zip
As WAR package only:
https://c2id-downloads.s3.eu-central-1.amazonaws.com/server/3.8/c2id.war https://c2id-downloads.s3.eu-central-1.amazonaws.com/server/3.8/c2id-3.8.war
Questions?
Please contact Connect2id support.
Connect2id Server 3.8 release notes
Configuration
-
/WEB-INF/oidcProvider.properties
* Adds new op.reg.ldapServer.responseTimeout property to configure an explicit timeout (in milliseconds) for responses from the LDAP directory server where client registrations are persisted. -
/WEB-INF/authzStore.properties
* Adds new authzStore.ldapServer.responseTimeout property to configure an explicit timeout (in milliseconds) for responses from the LDAP directory server where long-lived authorisations are persisted. -
/WEB-INF/monitor.properties
* Adds new monitor.graphite.* properties to enable and configure reporting Connect2id server metrics to a Graphite / Carbon server. Includes support for prefix / API key setting, time unit conversion and metric name filtering. -
/WEB-INF/web.xml
* The com.nimbusds.common.servlet.MonitorLauncher servlet context listener is invoked last to facilitate logging of all metrics names for reporting via Graphite.
Web API
-
/clients
* Allows initial registration access tokens to specify the scope values that may be registered by the client. These are specified by giving the initial registration access token scope values of the form `client-reg:scope:[scope-value]` where `[scope-value]` denotes the permitted scope value that may be registered. For example, to allow a client to register for the *openid* and *email* scopes, create an initial registration token with the following scope: `client-reg:scope:openid client-reg:scope:email`.
Bug fixes
- Ensures all paged LDAP searches that belong to a particular LDAP search request are performed on the same checked out LDAP connection (issues authz-store/109 and server/183).
Dependencies
-
Adds dependency to io.dropwizard.metrics:metrics-graphite:3.1.2
-
Upgrades to com.nimbusds:oauth2-authz-store:3.3
-
Upgrades to com.nimbusds:oidc-session-store:3.3
-
Upgrades to com.nimbusds:oauth2-oidc-sdk:5.1.1
-
Upgrades to com.nimbusds:common:1.98.1
-
Upgrades to com.thetransactioncompany:java-property-utils:1.10