DPoP tokens with the OpenID Connect developer client
Our open source web client for testing OpenID Connect compliant providers received an update to handle DPoP tokens.

DPoP is a new type of OAuth 2.0 token, designed primarily for Single Page Applications (SPAs) and with higher-grade security than the common Bearer tokens. The extra DPoP security makes the token “sender-constrained”, by binding it to a private RSA or EC key that belongs to the client. A DPoP token that is leaked, by accident or through some malicious action, cannot be used on its own (as opposed to Bearer tokens). For a client to use a DPoP token at the intended endpoint it must also possess the private binding key and this key can be generated and stored via the SubtleCrypto API in a way that prevents its extraction from the browser.
Note, the DPoP token is not a security cure for buggy or vulnerable JavaScript code in a SPA! If the SPA is taken over in a XSS attack the malicious code may perform all the necessary operations to impersonate the legitimate user without exfiltrating the private key.
You can test DPoP in our online demo against the most recent Connect2id server release (v12.2):
| Client URL | https://demo.c2id.com/oidc-client/ |
|---|
To trigger a request for a DPoP token click on the Options “Show” button, then
select a JWS algorithm for the DPoP proof, a signed JWT used to Demonstrate
Proof-of-Possession (DPoP) of the key at the OAuth 2.0 server. You can select
RS256 or any other JWS algorithm that is supported by the server.
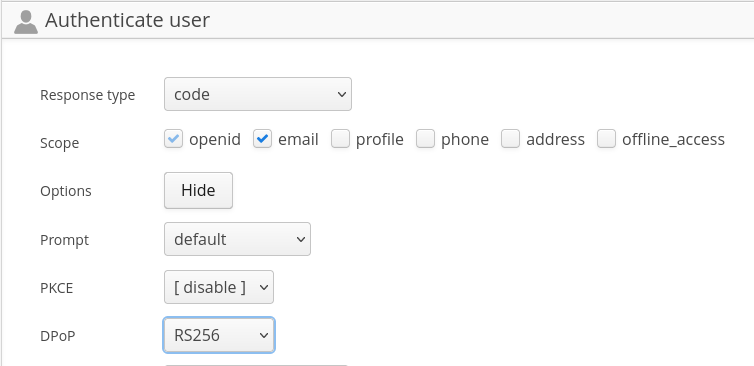
When done click on “Authenticate with OpenID Connect” and follow the flow through the login and consent screens on the server.
The type of the returned access token is shown in the standard token_type
parameter:
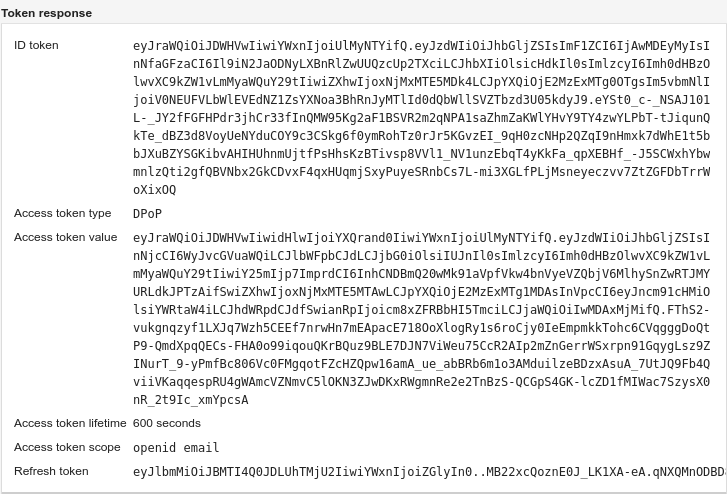
If the server issued a refresh token, and the OAuth 2.0 client / OpenID relying party is public (as an SPA technically is, because it has no authenticating client credentials), the refresh token will also be DPoP bound, just like the access token, to prevent its use in case of a leak.
This web client is built with the open source OAuth 2.0 / OpenID Connect SDK, which implements all standards in the OAuth 2.0 and OpenID Connect space, and the majority of drafts in development. Feel free to fork it or contribute if you have ideas!
To join the DPoP discussion check out the OAuth WG mailing list.